Navigating Windows Server 2025 In A Post-TPM World: Understanding The Implications And Exploring Alternatives
Navigating Home windows Server 2025 in a Submit-TPM World: Understanding the Implications and Exploring Options
Associated Articles: Navigating Home windows Server 2025 in a Submit-TPM World: Understanding the Implications and Exploring Options
Introduction
With enthusiasm, let’s navigate by the intriguing subject associated to Navigating Home windows Server 2025 in a Submit-TPM World: Understanding the Implications and Exploring Options. Let’s weave fascinating data and provide contemporary views to the readers.
Desk of Content material
Navigating Home windows Server 2025 in a Submit-TPM World: Understanding the Implications and Exploring Options
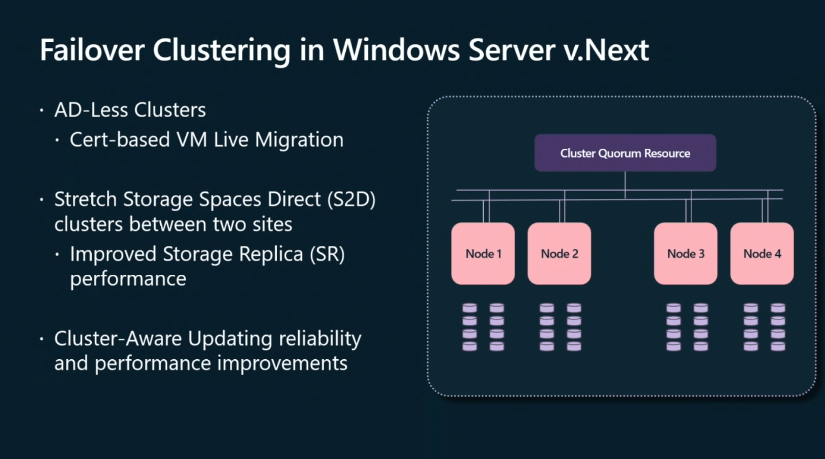
The panorama of cybersecurity is continually evolving, and with it, the necessities for safe computing environments. One of the vital distinguished shifts in recent times has been the rising emphasis on hardware-based safety measures, exemplified by the rising prominence of Trusted Platform Modules (TPMs). Whereas TPMs provide important benefits in securing techniques, their absence in legacy {hardware} or particular situations presents a singular problem for organizations searching for to leverage the capabilities of Home windows Server 2025.
This text delves into the implications of deploying Home windows Server 2025 on techniques with out TPMs, exploring the underlying safety concerns and potential workarounds. We are going to analyze the advantages of TPMs, talk about the restrictions they impose on older {hardware}, and examine various safety methods that may be carried out to take care of a sturdy and safe atmosphere.
The Significance of TPMs in Fashionable Safety
Trusted Platform Modules (TPMs) are specialised cryptographic chips embedded inside pc techniques. They play an important function in enhancing safety by offering a safe atmosphere for storing and managing cryptographic keys, facilitating safe boot processes, and enabling hardware-based encryption.
Key Advantages of TPMs:
- Safe Boot: TPMs make sure that solely trusted working techniques and functions are loaded in the course of the boot course of, stopping malicious software program from compromising the system earlier than it may be detected.
- BitLocker Encryption: TPMs act as a hardware-based key protector for BitLocker Drive Encryption, making it considerably tougher for unauthorized customers to entry encrypted knowledge.
- Password Administration: TPMs can securely retailer consumer passwords, stopping them from being compromised within the occasion of a system breach.
- Enhanced Authentication: TPMs allow stronger authentication mechanisms, akin to Home windows Good day for Enterprise, which makes use of facial recognition or fingerprint scanning for safe login.
Challenges of TPM-less Environments
Whereas TPMs provide important safety enhancements, their absence can current challenges for organizations:
- Legacy {Hardware}: Many older techniques lack TPMs, making it tough to implement the most recent security measures, together with safe boot and BitLocker encryption.
- Value Issues: Upgrading present {hardware} to incorporate TPMs is usually a expensive endeavor, particularly for big organizations with intensive server infrastructure.
- Restricted Performance: With out a TPM, sure security measures, akin to Home windows Good day for Enterprise and a few superior authentication protocols, will not be absolutely useful.
Navigating Home windows Server 2025 With out TPMs: Exploring Options
Regardless of the challenges, organizations can nonetheless deploy Home windows Server 2025 on techniques with out TPMs whereas sustaining a excessive degree of safety. This requires a complete strategy that leverages a mix of software-based options, safety greatest practices, and various safety measures.
Software program-Primarily based Options:
-
Home windows Server 2025 Safety Options: Home windows Server 2025 gives a sturdy set of built-in security measures that may be successfully utilized even with out a TPM. These embody:
- Sturdy Passwords and Multi-Issue Authentication: Implement robust password insurance policies and implement multi-factor authentication (MFA) to strengthen consumer accounts.
- Group Coverage and Consumer Rights Administration: Make the most of Group Coverage to configure safety settings and limit consumer privileges, limiting the potential impression of malicious exercise.
- Safety Updates and Patching: Hold techniques up to date with the most recent safety patches to deal with vulnerabilities and mitigate potential threats.
- Anti-Malware and Endpoint Safety: Implement sturdy anti-malware options and endpoint safety software program to detect and forestall malware infections.
- Various Encryption Options: Whereas BitLocker Drive Encryption closely depends on TPMs, various encryption options, akin to VeraCrypt or LUKS, may be employed to safe knowledge on techniques with out TPMs.
Safety Finest Practices:
- Community Segmentation: Isolate delicate techniques and functions on separate networks to restrict the potential impression of breaches.
- Firewall Configuration: Configure firewalls to dam unauthorized community entry and filter visitors primarily based on particular safety guidelines.
- Knowledge Backup and Restoration: Implement common knowledge backup and restoration procedures to reduce knowledge loss within the occasion of a safety incident.
- Safety Consciousness Coaching: Educate customers about widespread safety threats and greatest practices for safeguarding delicate data.
Various Safety Measures:
- Virtualization and Containerization: Leverage virtualization and containerization applied sciences to isolate functions and techniques, lowering the potential impression of safety breaches.
- {Hardware} Safety Modules (HSMs): HSMs present a hardware-based safety answer that can be utilized as a substitute for TPMs for safe key administration and encryption.
- Safe Enclaves: Fashionable processors usually embody safe enclaves, that are remoted areas inside the processor that can be utilized to guard delicate knowledge and computations.
FAQs
Q: Can I nonetheless use BitLocker Drive Encryption with out a TPM?
A: Whereas BitLocker Drive Encryption is designed to leverage TPMs for key safety, it may be utilized in a "TPM-less" mode. This mode makes use of a restoration password or a USB key to encrypt and decrypt the drive. Nonetheless, it is very important observe that this mode is much less safe than utilizing a TPM, because the restoration password or USB key may be compromised.
Q: What are the dangers related to utilizing Home windows Server 2025 with out a TPM?
A: Utilizing Home windows Server 2025 with out a TPM can enhance the danger of safety breaches, because it eliminates the hardware-based safety measures offered by TPMs. This could make techniques extra weak to malicious software program, unauthorized entry, and knowledge theft.
Q: Are there any particular security measures that shall be unavailable with out a TPM?
A: Some security measures, akin to Home windows Good day for Enterprise and sure superior authentication protocols, rely closely on TPMs and will not be absolutely useful with out them.
Q: What are some greatest practices for securing a Home windows Server 2025 system with out a TPM?
A: Implementing robust password insurance policies, enabling multi-factor authentication, using Group Coverage to limit consumer privileges, and holding the system up to date with the most recent safety patches are important practices for securing a Home windows Server 2025 system with out a TPM.
Ideas
- Assess Your Safety Wants: Fastidiously consider your particular safety necessities and decide the extent of safety that’s crucial to your atmosphere.
- Think about {Hardware} Upgrades: If doable, contemplate upgrading older techniques to incorporate TPMs to learn from the improved security measures they supply.
- Implement a Layered Safety Strategy: Make the most of a mix of software-based options, safety greatest practices, and various safety measures to create a sturdy and multi-layered safety technique.
- Keep Knowledgeable About Safety Tendencies: Hold abreast of rising safety threats and vulnerabilities to proactively tackle potential dangers.
Conclusion
The absence of TPMs in legacy {hardware} or particular deployment situations doesn’t preclude organizations from leveraging the capabilities of Home windows Server 2025. By implementing a complete strategy that mixes software-based options, safety greatest practices, and various safety measures, organizations can preserve a excessive degree of safety and defend their techniques from potential threats. Whereas TPMs provide important benefits, their absence doesn’t necessitate a compromise in safety. By embracing a proactive and knowledgeable strategy, organizations can successfully safe their Home windows Server 2025 environments even with out TPMs, making certain the integrity and confidentiality of their knowledge.




Closure
Thus, we hope this text has offered priceless insights into Navigating Home windows Server 2025 in a Submit-TPM World: Understanding the Implications and Exploring Options. We thanks for taking the time to learn this text. See you in our subsequent article!