Mastering The Realm: A Comprehensive Guide To Windows Server Kerberos Configuration
Mastering the Realm: A Complete Information to Home windows Server Kerberos Configuration
Associated Articles: Mastering the Realm: A Complete Information to Home windows Server Kerberos Configuration
Introduction
With nice pleasure, we’ll discover the intriguing matter associated to Mastering the Realm: A Complete Information to Home windows Server Kerberos Configuration. Let’s weave fascinating data and supply contemporary views to the readers.
Desk of Content material
Mastering the Realm: A Complete Information to Home windows Server Kerberos Configuration
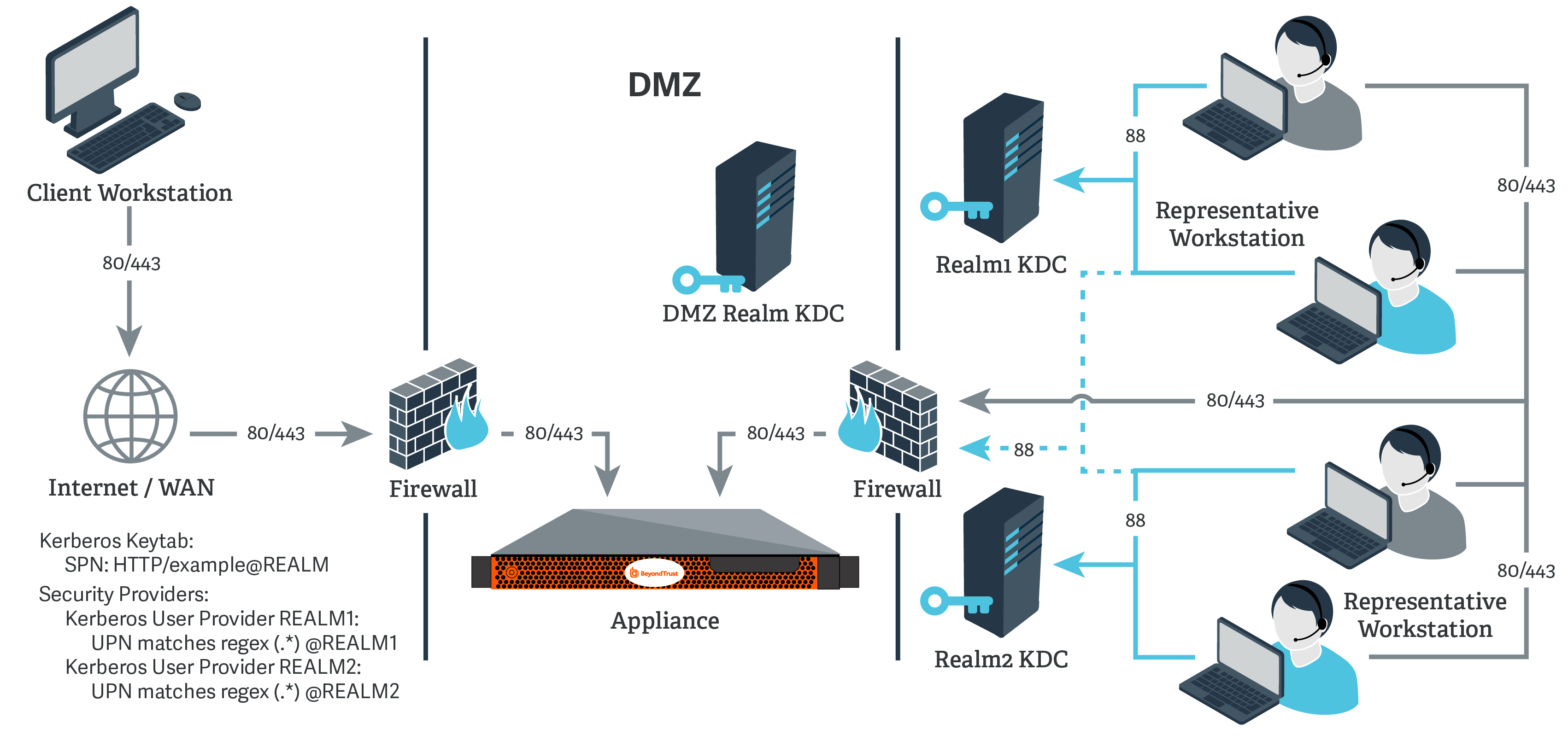
Kerberos, a strong authentication protocol, varieties the bedrock of safe communication inside a Home windows Lively Listing atmosphere. Its position in guaranteeing safe entry to assets, providers, and information is paramount, making a deep understanding of its configuration essential for any system administrator. This text delves into the intricacies of Home windows Server Kerberos configuration, offering a complete information to its implementation, troubleshooting, and optimization.
The Essence of Kerberos: A Safe Authentication Framework
At its core, Kerberos operates on the precept of "mutual authentication," the place each the shopper and server confirm one another’s identities earlier than granting entry to assets. This course of depends on a safe, centralized system often called the Key Distribution Heart (KDC), which acts because the trusted authority inside the area.
Key Parts of the Kerberos Ecosystem:
- Key Distribution Heart (KDC): The central authority accountable for issuing and managing safety keys (often called tickets) for customers and providers. It consists of two principal elements: the Authentication Server (AS) and the Ticket Granting Server (TGS).
- Authentication Server (AS): Handles the preliminary authentication request from a shopper, verifying the shopper’s credentials and issuing a Ticket Granting Ticket (TGT).
- Ticket Granting Server (TGS): Grants entry to particular providers based mostly on the TGT supplied by the AS. It points Service Tickets, permitting purchasers to entry particular assets.
- Purchasers: Customers or purposes requesting entry to community assets.
- Servers: Providers or purposes that present entry to assets.
The Circulate of Kerberos Authentication:
- Preliminary Authentication: A shopper requests entry to a service.
- TGT Acquisition: The shopper sends a request to the AS, offering its username and password. The AS verifies the credentials and points a TGT, encrypted with the shopper’s distinctive secret key.
- Service Ticket Request: The shopper presents the TGT to the TGS, requesting a Service Ticket for a selected service.
- Service Ticket Issuance: The TGS verifies the TGT, retrieves the service’s data, and generates a Service Ticket, encrypted with the service’s secret key.
- Service Entry: The shopper presents the Service Ticket to the service, permitting entry to the requested useful resource.
Configuration Necessities for a Strong Kerberos Atmosphere:
1. Area Controller (DC) Configuration:
- Area Naming Context (DNS): Guarantee correct DNS configuration for the area, permitting purchasers to resolve the KDC’s hostname and IP handle.
- Kerberos Area Controller Settings: Configure settings such because the Kerberos realm, most ticket lifetime, and different domain-wide parameters.
- Time Synchronization: Correct time synchronization throughout all DCs is crucial for Kerberos to operate accurately. Configure a time supply like Community Time Protocol (NTP) for correct timekeeping.
2. Shopper and Server Configuration:
- Kerberos Shopper Settings: Configure purchasers to belief the KDC and guarantee correct communication with the area.
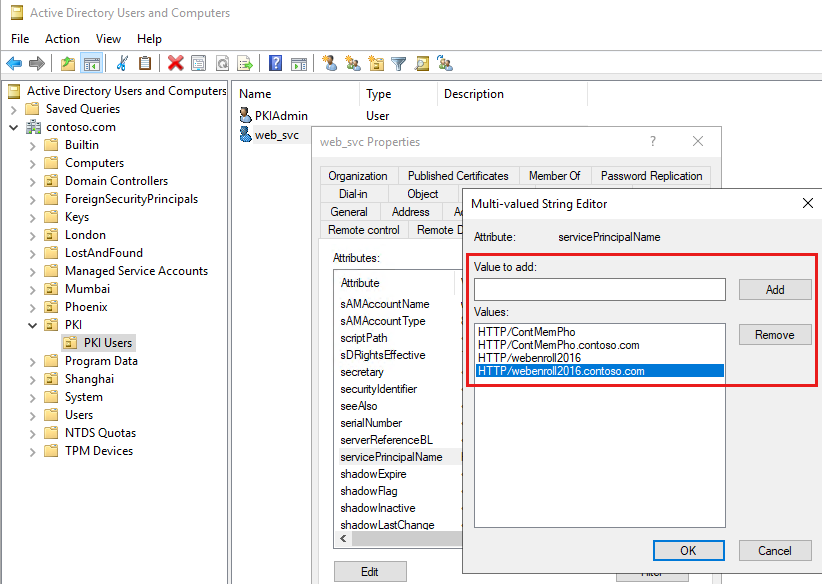
- Kerberos Service Principal Names (SPNs): SPNs uniquely determine providers inside the area. Configure SPNs for all providers that require Kerberos authentication, guaranteeing correct mapping between the service and its corresponding account.
- Service Account Configuration: Create service accounts with applicable permissions and configure them to make use of Kerberos authentication.
3. Safety and Finest Practices:
- Sturdy Passwords: Implement robust password insurance policies for consumer accounts and repair accounts.
- Account Lockout Insurance policies: Configure account lockout insurance policies to stop unauthorized entry makes an attempt.
- Kerberos Delegation: Make the most of Kerberos delegation to permit providers to behave on behalf of customers, simplifying authentication for complicated eventualities.
- Kerberos Auditing: Implement Kerberos auditing to observe authentication occasions and determine potential safety vulnerabilities.
Troubleshooting Kerberos Points:
- Occasion Viewer: Use the Occasion Viewer to investigate Kerberos-related occasions, offering precious insights into authentication failures.
- Kerberos Instruments: Make the most of built-in instruments like Klist and Setspn to diagnose and handle Kerberos configuration.
- Community Connectivity: Guarantee correct community connectivity between purchasers, servers, and the KDC.
- Time Synchronization: Confirm correct time synchronization throughout all elements of the area.
Incessantly Requested Questions (FAQs):
Q: What’s the goal of Kerberos?
A: Kerberos is a community authentication protocol designed to supply safe entry to community assets. It makes use of a system of tickets and secret keys to confirm the id of each purchasers and servers, guaranteeing safe communication and entry management.
Q: Why is Kerberos necessary for Home windows Server?
A: Kerberos is crucial for Home windows Server as a result of it supplies a safe and dependable authentication mechanism for accessing assets inside a site. It protects delicate information, ensures consumer accountability, and simplifies entry management administration.
Q: What are the advantages of utilizing Kerberos?
A: Kerberos presents a number of advantages, together with:
- Sturdy Authentication: Offers safe authentication based mostly on mutual verification of identities.
- Centralized Administration: Permits for centralized administration of authentication insurance policies and credentials.
- Scalability: Simply scales to accommodate massive and complicated networks.
- Interoperability: Works seamlessly with different Home windows providers and purposes.
Q: How do I configure Kerberos on a Home windows Server?
A: Configuring Kerberos includes configuring the area controller, shopper machines, and providers. This sometimes contains establishing DNS, creating service accounts, and configuring SPNs.
Q: What are some frequent Kerberos troubleshooting strategies?
A: Troubleshooting Kerberos points usually includes analyzing Occasion Viewer logs, utilizing Kerberos instruments like Klist and Setspn, and checking community connectivity and time synchronization.
Suggestions for Optimizing Kerberos Configuration:
- Use a devoted area controller for Kerberos operations.
- Configure Kerberos delegation for providers that must entry assets on behalf of customers.
- Implement Kerberos auditing to observe authentication occasions and determine potential vulnerabilities.
- Frequently evaluation and replace Kerberos settings to make sure optimum safety and efficiency.
Conclusion:
Kerberos stands as a cornerstone of safety inside a Home windows Lively Listing atmosphere. Understanding its configuration, troubleshooting strategies, and finest practices is crucial for system directors in search of to take care of a strong and safe community infrastructure. By mastering the realm of Kerberos, directors can guarantee safe entry to assets, shield delicate information, and improve the general safety posture of their community.
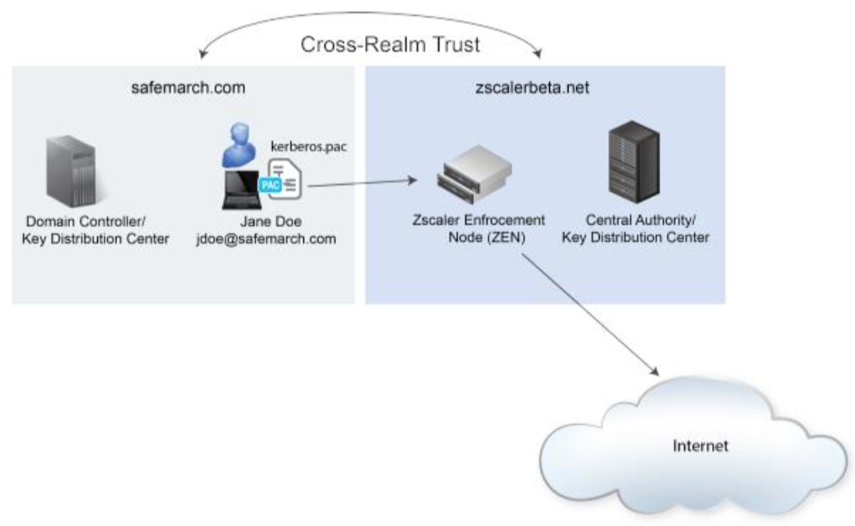

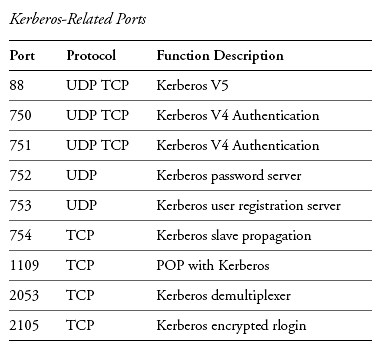


Closure
Thus, we hope this text has supplied precious insights into Mastering the Realm: A Complete Information to Home windows Server Kerberos Configuration. We hope you discover this text informative and useful. See you in our subsequent article!